Apache Guacamole isn’t your average avocado dip; it’s a powerful open-source tool that lets you access remote desktops from practically anywhere. This versatile application provides a secure and flexible way to connect to various systems using different protocols, all through a single, web-based interface. We’ll explore its architecture, security features, and how to set it up and optimize its performance for a smooth remote access experience.
Table of Contents
Imagine a world without clunky VPNs or complex desktop sharing software. Guacamole offers a streamlined approach to remote access, consolidating connections to RDP, VNC, SSH, and more. This guide dives deep into its capabilities, explaining its inner workings and demonstrating how to leverage its full potential for efficient and secure remote management.
Apache Guacamole’s Architecture
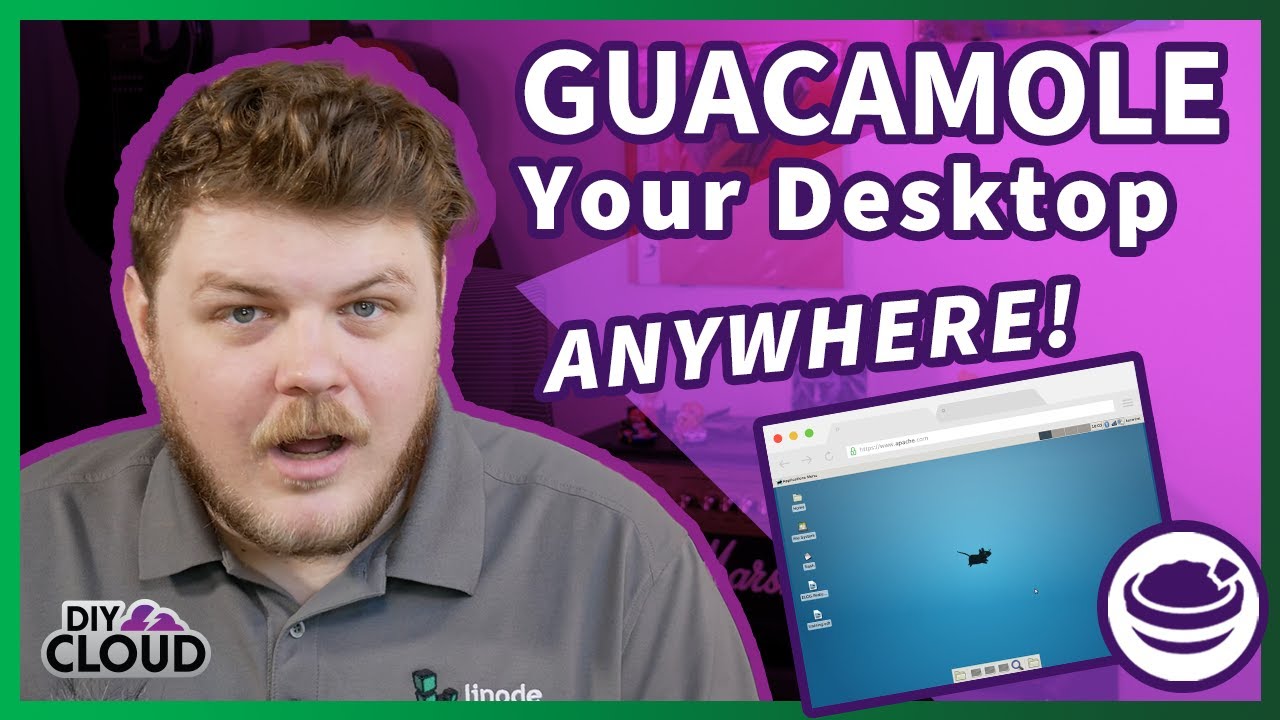
Apache Guacamole employs a robust client-server architecture, allowing users to access remote desktops and applications securely from various devices. This architecture is key to its flexibility and scalability, enabling support for a wide range of protocols and client platforms. The core principle is separating the user interface (the client) from the connection management and protocol handling (the server), enhancing security and maintainability.The Guacamole server acts as the central hub, managing all connections and translating client requests into actions on the remote server.
It doesn’t directly interact with the remote desktop; instead, it acts as a secure intermediary, handling authentication, authorization, and the complex protocol conversions necessary to bridge the gap between the client and the remote resources. This approach ensures that sensitive connection details are never exposed directly to the client.
Guacamole Server’s Role in Connection Management
The Guacamole server is responsible for several crucial aspects of connection management. It handles user authentication and authorization, ensuring only authorized users can access specific resources. It also manages the lifecycle of each connection, from initial establishment to termination. This includes handling connection pooling, load balancing, and resource allocation to optimize performance and resource utilization. Furthermore, the server handles the complex protocol translations required to connect to various remote desktop and application protocols such as VNC, RDP, SSH, and more.
This protocol translation is a core feature of Guacamole, providing a unified interface for accessing diverse remote resources.
Components of a Typical Guacamole Deployment
A typical Guacamole deployment involves several key components working in concert. These components interact to provide a seamless remote access experience. First, there is the Guacamole server itself, which is the central component responsible for connection management and protocol translation. Then, there are the remote desktops or applications, which are the target resources accessed by users. These could be physical or virtual machines running various operating systems.
Next, you have the Guacamole client, which is the user interface used to access the remote resources. This can be a web browser or a dedicated client application. Finally, there are supporting infrastructure components like a database (for user management and connection details) and potentially a load balancer (for distributing connections across multiple Guacamole servers).
Data Flow Diagram
Imagine a diagram with three main blocks: the Guacamole Client (a web browser, for example), the Guacamole Server, and the Remote Desktop Server (hosting the target application or desktop). The client initiates a connection request to the Guacamole server. This request includes authentication credentials. The Guacamole server verifies these credentials against its user database. Upon successful authentication, the server establishes a connection to the remote desktop server using the appropriate protocol (RDP, VNC, etc.).
Data streams from the remote desktop server are then received by the Guacamole server, translated into a format compatible with the client, and relayed to the client’s browser. Conversely, user input from the client is received by the Guacamole server, translated, and sent to the remote desktop server. This constant bidirectional data flow enables real-time interaction with the remote desktop or application.
The entire process is secured through encryption, protecting the data exchanged between all three components.
Guacamole’s Supported Protocols
Guacamole’s strength lies in its ability to seamlessly connect to a variety of remote desktop protocols, offering users flexibility and broad compatibility. This allows access to diverse systems without needing separate clients for each protocol, simplifying the user experience and centralizing management. Understanding the nuances of each supported protocol is crucial for choosing the right connection method for specific needs, considering factors like performance, security, and the target system’s capabilities.Guacamole supports a range of protocols, each with its own strengths and weaknesses regarding security and performance.
The most common include RDP, VNC, SSH, and Telnet. Let’s delve into a comparison of these protocols to highlight their characteristics within the Guacamole framework.
RDP (Remote Desktop Protocol)
RDP is Microsoft’s proprietary protocol, primarily used for connecting to Windows machines. It’s widely adopted and generally offers good performance, especially on local networks. However, its security has been a concern historically, with vulnerabilities exploited in the past. Modern implementations include encryption, improving security significantly, but proper configuration remains vital. RDP’s biggest advantage is its tight integration with the Windows ecosystem and its ability to handle complex features like sound redirection and clipboard sharing effectively.
A disadvantage is its limited cross-platform support outside of Microsoft’s own products and its reliance on proprietary technology, potentially raising licensing issues in certain contexts.
VNC (Virtual Network Computing)
VNC is an open-source protocol offering cross-platform compatibility. It’s relatively simple to set up and use, making it a popular choice for remote access to various operating systems. However, VNC’s performance can be slower than RDP, particularly over high-latency connections, due to its reliance on less efficient encoding methods. Security is a key concern with VNC, as unencrypted connections are vulnerable to eavesdropping and man-in-the-middle attacks.
While encryption is available, it’s not always enabled by default, highlighting the importance of proper configuration for secure usage.
SSH (Secure Shell)
SSH is a powerful and secure protocol primarily used for command-line access but also capable of supporting graphical environments through X11 forwarding. Its strong encryption makes it highly secure, protecting data transmitted between client and server. Performance is generally good, especially for text-based interactions. However, the initial setup can be more complex than RDP or VNC, requiring a deeper understanding of command-line interfaces.
Furthermore, X11 forwarding, while enabling graphical access, can introduce performance overhead and security considerations if not properly configured.
Telnet
Telnet is an older, insecure protocol that should generally be avoided in modern environments. It transmits data in plain text, making it highly vulnerable to eavesdropping and attacks. While Guacamole supports it for legacy systems, its use is strongly discouraged due to its lack of security features. Performance is generally adequate for text-based interaction, but its inherent security risks outweigh any performance benefits.
Protocol Comparison Table
| Protocol | Performance | Security (with proper config) | Cross-Platform Compatibility |
|---|---|---|---|
| RDP | Good (especially LAN) | Good (with encryption) | Limited (primarily Windows) |
| VNC | Moderate (can be slow over WAN) | Moderate (encryption crucial) | Excellent |
| SSH | Good (text-based; X11 forwarding can impact performance) | Excellent | Excellent |
| Telnet | Adequate (text-based) | Very Poor (unencrypted) | Excellent |
Guacamole Security Features
Guacamole’s security is paramount, given its role in providing remote access to various systems. It employs a multi-layered approach to protect both the Guacamole server and the resources accessed through it. Understanding these features and implementing best practices is crucial for a secure deployment.Guacamole’s built-in security mechanisms focus on authentication, authorization, and data encryption. Authentication verifies the user’s identity, authorization controls access to specific resources, and encryption protects data in transit and, in some cases, at rest.
These mechanisms work together to create a robust security posture.
Authentication Methods
Guacamole supports a variety of authentication methods, allowing for flexible integration with existing infrastructure. This ensures that you can leverage your organization’s established identity management system. The choice of authentication method depends on your specific security requirements and existing infrastructure.
- Built-in User Database: A simple, internal database for managing users and passwords. Suitable for small deployments or testing environments, but generally not recommended for production due to limited scalability and security features compared to external authentication mechanisms.
- LDAP: Allows Guacamole to authenticate users against an existing Lightweight Directory Access Protocol (LDAP) server. This offers centralized user management and simplifies administration for larger organizations.
- Kerberos: Provides strong authentication using Kerberos tickets, enhancing security by eliminating the need to transmit passwords over the network. This is ideal for environments with high security needs.
- OAuth 2.0: Enables authentication through a third-party provider, such as Google, GitHub, or other identity providers, offering a convenient and secure way for users to log in using their existing accounts.
Authorization and Access Control
Beyond authentication, Guacamole offers robust authorization mechanisms to control user access to specific resources. This granular control prevents unauthorized users from accessing sensitive systems or data.Guacamole’s connection definitions can be configured to restrict access based on user groups or roles. For example, you can create a group of users who only have access to specific virtual desktops or applications.
This prevents unauthorized access to sensitive systems, improving overall security. The implementation details of this vary depending on the chosen authentication backend (e.g., using LDAP groups or Guacamole’s built-in roles).
Data Encryption
Guacamole uses TLS encryption to secure communication between the client and the server. This protects user credentials and all data transmitted during the session from eavesdropping. It is crucial to configure Guacamole to use strong TLS ciphers and to keep the server’s TLS certificates up-to-date. Additionally, depending on the protocol used, data encryption might also occur at the protocol level.
For example, RDP already includes encryption, but ensuring TLS encryption between Guacamole and the RDP server adds an additional layer of security.
Integration with Existing Security Infrastructure
Integrating Guacamole with your existing security infrastructure is a key step in ensuring a secure deployment. This integration can streamline user management and enhance overall security. Proper configuration is essential for seamless and secure operation.
- LDAP Integration: By configuring Guacamole to use your existing LDAP server, you centralize user management and leverage existing authentication and authorization mechanisms. This reduces administrative overhead and improves security by using a well-established system.
- Kerberos Integration: Similar to LDAP, integrating with Kerberos provides strong authentication and single sign-on capabilities. This eliminates the need for users to remember separate passwords for Guacamole and other systems.
- Firewall Configuration: Restricting access to the Guacamole server through a firewall is essential. Only allow connections from trusted networks and IP addresses. This prevents unauthorized access to the server and the resources it manages.
Guacamole Installation and Configuration: Apache Guacamole
Setting up Guacamole on a Linux server is a relatively straightforward process, but requires careful attention to detail, especially regarding security. This section details the installation and configuration steps, emphasizing best practices for a secure deployment. We’ll cover installation on a Debian-based system (like Ubuntu or Debian), but the general principles apply to other Linux distributions with minor adjustments.
The installation process involves several steps: downloading the necessary packages, configuring the database, setting up Guacamole itself, and finally, configuring users and permissions. Proper configuration is key to ensuring both functionality and security.
Guacamole Installation on Debian/Ubuntu
Before beginning, ensure your server has a recent version of Java installed (OpenJDK 11 or later is recommended). You’ll also need a database; PostgreSQL is a popular and secure choice. These prerequisites need to be installed and configured
-before* proceeding with the Guacamole installation.
- Update the package list:
sudo apt update - Install required packages: This will vary slightly depending on your database choice. For PostgreSQL, the command would be similar to:
sudo apt install tomcat9 guacamole-server postgresql postgresql-contrib. Remember to replacetomcat9with your preferred servlet container version if needed. - Configure PostgreSQL: Create a database user and database specifically for Guacamole. Use strong, unique passwords. A typical command might look like:
sudo -u postgres psql -c "CREATE USER guacamole WITH PASSWORD 'your_strong_password'; CREATE DATABASE guacamole OWNER guacamole;"Replaceyour_strong_passwordwith a robust password. - Install Guacamole client: This step is optional, allowing users to access Guacamole via a web interface. It can be done using the package manager, similar to the server installation.
- Configure Guacamole: The Guacamole configuration files are typically located in
/etc/guacamole/. The primary configuration file isguacamole.properties. You’ll need to adjust settings such as the database connection details (hostname, port, database name, username, and password) to match your PostgreSQL setup. Also ensure you adjust the server’s hostname/IP address in the properties file for correct client access.
Guacamole User Account and Permission Setup
After installation, you need to create user accounts and define their permissions. Guacamole offers robust access control, allowing granular management of which users can access which resources. This is crucial for maintaining security and ensuring only authorized personnel have access to sensitive systems.
- Access the Guacamole administration interface: This is usually accessible through a web browser at a URL like
https://your_server_ip:8080/guacamole/(adjust the port if necessary). - Create users: The admin interface allows you to create new users. Assign each user a strong, unique password. Avoid using easily guessable passwords or reusing passwords from other systems.
- Define connections: Guacamole connects to various protocols (RDP, VNC, SSH, etc.). You define these connections within the admin interface. Each connection requires specific configuration details, such as the hostname or IP address of the target server, the port, and any necessary authentication credentials.
- Assign permissions: Grant users permission to access only the connections they need. This principle of least privilege is fundamental to security.
Essential Post-Installation Security Measures
Securing your Guacamole installation after deployment is critical. Neglecting these steps can leave your server and connected systems vulnerable to attack.
- Enable HTTPS: Use a valid SSL/TLS certificate to encrypt all communication between clients and the Guacamole server. This prevents eavesdropping and man-in-the-middle attacks.
- Restrict network access: Configure your firewall to allow only necessary traffic to the Guacamole server. Block all other inbound connections.
- Regular security updates: Keep Guacamole and its dependencies up-to-date with the latest security patches. This mitigates known vulnerabilities.
- Strong passwords and authentication: Enforce strong password policies for all users and consider implementing multi-factor authentication (MFA) for added security.
- Regular security audits: Periodically review user permissions and connections to ensure they remain appropriate and no unauthorized access exists.
- Monitor logs: Regularly examine Guacamole’s logs for any suspicious activity.
Guacamole Scalability and Performance
Guacamole’s ability to handle a large number of concurrent users and maintain acceptable performance is crucial for its success in enterprise environments. Several factors influence Guacamole’s scalability and performance, including the underlying infrastructure, the number and type of connections, and the complexity of the remote desktops being accessed. Optimizing these aspects is key to a smooth and responsive user experience.Optimizing Guacamole performance requires a multi-faceted approach.
Simply throwing more hardware at the problem isn’t always the best solution; understanding the bottlenecks and addressing them strategically is far more effective.
Guacamole Performance Optimization Techniques
Several techniques can significantly improve Guacamole’s performance. These optimizations target different aspects of the system, from network configuration to resource allocation within the Guacamole server itself.
- Efficient Network Configuration: Proper network configuration is paramount. Using a high-bandwidth, low-latency network connection between the Guacamole server and the remote desktops is essential. Consider using dedicated network segments for Guacamole traffic to avoid congestion from other applications. Implementing Quality of Service (QoS) policies can prioritize Guacamole traffic over other network activities. For example, prioritizing UDP packets over TCP packets for video streaming can improve visual quality.
- Hardware Upgrades: While not always the first step, upgrading the hardware of the Guacamole server can drastically improve performance. This includes increasing CPU cores, RAM, and network interface card (NIC) bandwidth. A server with multiple high-performance CPUs, ample RAM (at least 16GB, more for larger deployments), and a 10 Gigabit Ethernet connection can handle significantly more concurrent users. The type of storage (SSD vs.
HDD) can also significantly impact performance. SSDs offer drastically faster read/write speeds.
- Guacamole Server Tuning: The Guacamole server itself has various configuration parameters that can be tuned for optimal performance. These parameters often relate to connection pooling, caching, and thread management. Careful adjustment of these parameters based on the specific workload and hardware can significantly improve responsiveness and throughput. For instance, increasing the number of worker threads can handle more concurrent connections but may require more system resources.
- Image Compression and Encoding: Guacamole uses various codecs for image compression and encoding. Choosing the right codec and optimizing its settings can significantly reduce bandwidth usage and improve performance. Experimentation with different codecs and their parameters (like quality settings) is crucial to find the optimal balance between visual quality and bandwidth consumption. For example, using a more efficient codec like VP9 over H.264 might reduce bandwidth usage while maintaining acceptable video quality.
Guacamole Scaling Strategies
Scaling Guacamole to handle a high number of concurrent users often involves distributing the workload across multiple servers. This can be achieved through various strategies.
- Horizontal Scaling with Load Balancers: Deploying multiple Guacamole servers behind a load balancer is a common and effective scaling strategy. The load balancer distributes incoming connections across the available servers, ensuring no single server becomes overloaded. This approach offers high availability and allows for easy addition of more servers as needed. A common load balancer configuration might use a round-robin algorithm to distribute connections evenly across servers.
- Vertical Scaling: While horizontal scaling is generally preferred, vertical scaling—upgrading the hardware of a single Guacamole server—can be a viable option for smaller deployments or as a temporary solution before implementing a more comprehensive scaling strategy. However, vertical scaling has limitations; there’s a practical limit to how much you can upgrade a single server before it becomes cost-prohibitive or faces performance limitations due to architectural constraints.
- Caching Mechanisms: Implementing caching mechanisms can significantly reduce the load on the Guacamole servers. Caching frequently accessed resources, such as images or configuration data, can minimize the number of requests to remote servers and databases, improving response times and reducing server load. Guacamole itself may offer some caching features, but additional caching layers can be implemented using a reverse proxy server like Nginx or Varnish.
Guacamole Performance Monitoring and Resource Utilization
Monitoring Guacamole’s performance and resource utilization is crucial for proactive identification and resolution of potential bottlenecks. Several tools and techniques can be used for this purpose.
- System Monitoring Tools: Standard system monitoring tools like Nagios, Zabbix, or Prometheus can be used to track key metrics such as CPU usage, memory consumption, network traffic, and disk I/O. These tools provide valuable insights into the overall health and performance of the Guacamole servers.
- Guacamole-Specific Metrics: Guacamole may provide its own metrics or logs that can be monitored. These metrics can include the number of active connections, connection latency, and error rates. Analyzing these metrics can provide valuable insights into Guacamole’s performance and identify areas for improvement. For example, a high connection latency might indicate network issues, while a high error rate might point to problems with the remote desktops or Guacamole configuration.
- Log Analysis: Regularly reviewing Guacamole’s logs can help identify errors and performance issues. Log analysis tools can help automate this process, allowing for quicker identification of potential problems. Analyzing logs can reveal patterns in errors, helping pinpoint issues that might be otherwise missed through basic system monitoring.
Guacamole Integration with Other Systems
Guacamole’s power extends far beyond its core functionality. Seamless integration with other systems is key to maximizing its value within a larger IT infrastructure. This section explores how Guacamole can be effectively integrated with single sign-on (SSO) solutions, monitoring tools, and centralized logging systems, enhancing security, manageability, and overall user experience.Integrating Guacamole with various systems streamlines administration and improves the overall user experience.
This allows for a more cohesive and efficient IT environment. Proper integration is vital for larger deployments and those with complex security needs.
Guacamole Integration with Single Sign-On (SSO) Solutions
Guacamole’s flexibility allows for integration with a variety of SSO solutions, eliminating the need for separate user credentials for accessing remote desktops. This significantly improves security and simplifies user management. Common approaches involve leveraging Guacamole’s authentication mechanisms to integrate with existing SSO providers like Okta, Keycloak, or Active Directory. This is typically accomplished by configuring Guacamole to authenticate users against a centralized identity provider.
The specific configuration steps vary depending on the chosen SSO solution, but generally involve setting up an authentication module within Guacamole to forward authentication requests to the SSO provider and receive authentication responses. For instance, with Okta, you would configure an OpenID Connect (OIDC) connector within Guacamole, specifying the Okta tenant URL, client ID, and client secret. Once configured, users will be redirected to Okta for authentication, and upon successful authentication, they’ll be granted access to Guacamole without needing to enter their credentials again.
Guacamole Integration with Monitoring and Management Tools
Integrating Guacamole with monitoring and management tools provides valuable insights into its performance and health. This allows administrators to proactively identify and address potential issues. Several approaches exist, including using Guacamole’s built-in metrics and APIs to feed data into existing monitoring systems such as Prometheus, Grafana, or Nagios. For example, you could use Guacamole’s REST API to collect metrics on connection counts, latency, and error rates, and then use a monitoring tool to visualize and alert on these metrics.
This enables real-time monitoring of Guacamole’s performance and facilitates timely intervention in case of issues. Another approach is to integrate Guacamole with a system management platform, allowing administrators to manage Guacamole alongside other IT assets within a unified console.
Guacamole Integration with a Centralized Logging System
Centralized logging provides a comprehensive view of Guacamole’s activity, facilitating security auditing, troubleshooting, and performance analysis. This is achieved by configuring Guacamole to forward its logs to a centralized logging system like ELK stack (Elasticsearch, Logstash, Kibana), Splunk, or Graylog. Guacamole’s logging configuration allows specifying the log level and output destination. By forwarding logs to a centralized system, administrators can search, filter, and analyze logs from various sources, including Guacamole, to identify patterns, detect anomalies, and gain valuable insights into system behavior.
This comprehensive logging improves security posture by providing detailed audit trails and aiding in incident response. For example, integrating with the ELK stack allows for powerful log analysis and visualization, providing valuable insights into user activity, connection issues, and security events.
Guacamole’s Extensibility
Guacamole’s architecture is designed with extensibility in mind, allowing administrators and developers to tailor its functionality to meet specific needs. This flexibility comes from a well-defined plugin architecture and a robust API, making it easy to integrate with existing systems and add new features without modifying the core Guacamole codebase. This approach ensures that Guacamole remains adaptable to evolving technologies and diverse deployment environments.Guacamole’s extensibility primarily relies on its plugin architecture.
Plugins are self-contained modules that extend Guacamole’s capabilities by adding support for new protocols, authentication methods, or even entirely new features. These plugins are typically implemented as Java classes that adhere to specific interfaces defined by the Guacamole framework. This modular design ensures that the core Guacamole application remains stable and maintainable while allowing for a wide range of customizations.
Developing Custom Guacamole Extensions
Developing a Guacamole extension involves creating a Java class that implements one or more of Guacamole’s defined interfaces. This class will contain the specific logic for the extension. For instance, a plugin adding support for a new protocol would implement the `GuacamoleProtocol` interface, handling the connection establishment, data transfer, and disconnection for that protocol. The plugin would then be packaged as a JAR file and deployed to Guacamole’s plugin directory.
Guacamole’s documentation provides detailed instructions and examples on how to create and deploy plugins. The process involves understanding Guacamole’s API, implementing the necessary interfaces, and adhering to Guacamole’s plugin deployment conventions.
Common Use Cases for Guacamole Extensions
Several common use cases highlight the value of Guacamole’s extensibility. One example is adding support for uncommon or proprietary protocols. Organizations might have legacy systems relying on protocols not natively supported by Guacamole. A custom plugin can bridge this gap, allowing access to these systems through the Guacamole interface. Another frequent application is integrating Guacamole with existing authentication systems.
So, Apache Guacamole, right? It’s awesome for remote desktop access, but sometimes I need to whip up a quick graphic for a presentation. That’s when I fire up corel draw x7 to create some killer visuals. Then, once I’ve got the perfect image, I can easily share it using my Guacamole connection – it’s a pretty sweet workflow, honestly.
Rather than relying solely on Guacamole’s built-in authentication mechanisms, a plugin could be developed to authenticate users against an organization’s existing LDAP or Active Directory infrastructure. Finally, custom plugins can provide enhanced logging and monitoring capabilities, allowing administrators to track Guacamole usage and identify potential issues more effectively. For example, a plugin could integrate with a centralized logging system or provide real-time performance metrics.
Troubleshooting Common Guacamole Issues
Guacamole, while generally robust, can sometimes present connection or performance challenges. This section Artikels common problems, their causes, and effective troubleshooting strategies. Understanding these issues will help you maintain a smoothly running Guacamole deployment.
Connection Problems
Connection failures are among the most frequent Guacamole issues. These problems often stem from misconfigurations or network connectivity problems. Successfully resolving these issues typically involves a systematic check of various components.
- Incorrect Connection Parameters: Verify the hostname or IP address, port number, and credentials (username and password) used to connect to the target server. A single typo can prevent a connection. Double-check these settings against the server’s configuration.
- Network Connectivity Issues: Ensure network connectivity between the Guacamole server, the client machine, and the target server. Check for firewalls blocking connections on the necessary ports (typically SSH, RDP, VNC, etc.). Ping tests to each server can help isolate network problems.
- Authentication Failures: If the connection attempt fails with an authentication error, ensure the username and password are correct and that the user has the necessary permissions on the target server. Check the server’s authentication logs for clues.
- Protocol-Specific Problems: Some connection issues are protocol-specific. For example, with RDP, ensure the RDP service is running on the target server and that the necessary RDP components are installed and configured correctly. Similar checks should be performed for other protocols like VNC or SSH.
Performance Bottlenecks, Apache guacamole
Slow performance in Guacamole can significantly impact user experience. Identifying and addressing performance bottlenecks is crucial for maintaining a responsive system. A variety of factors can contribute to slow performance.
- Server Resource Constraints: A Guacamole server with insufficient CPU, memory, or network bandwidth can lead to slow connections and poor performance. Monitor server resource usage (CPU, memory, network I/O) to identify potential bottlenecks. Consider upgrading server hardware or optimizing Guacamole’s configuration to improve resource utilization.
- Network Latency: High network latency between the Guacamole server, the client, and the target server can result in sluggish performance. Investigate network paths and identify any potential bottlenecks. Using a network monitoring tool can help pinpoint slow links or congested network segments.
- Guacamole Server Configuration: Improperly configured Guacamole settings, such as insufficient connection pooling or inadequate caching, can negatively impact performance. Review Guacamole’s configuration files and adjust settings as needed to optimize performance. Consult the Guacamole documentation for recommended configuration values.
- Target Server Performance: The performance of the target server itself can also affect Guacamole’s responsiveness. If the target server is slow or overloaded, it will likely impact the Guacamole connection. Monitor the target server’s resource usage and address any performance issues on that server.
Common Guacamole Errors
Guacamole may occasionally produce error messages that require further investigation. Understanding these errors can help quickly resolve the underlying problem.
- “Connection Failed”: This generic error message requires further investigation. Check the Guacamole logs for more specific error details. The logs might indicate problems with network connectivity, authentication, or protocol-specific issues.
- “Authentication Failed”: This indicates a problem with user credentials or permissions on the target server. Verify the username and password and check the target server’s authentication logs.
- “Unsupported Protocol”: This error means Guacamole doesn’t support the protocol used by the target server. Ensure the target server uses a supported protocol (RDP, VNC, SSH, etc.).
- “Connection Timed Out”: This usually indicates a network connectivity problem. Check the network connection between the Guacamole server, the client, and the target server. Ensure firewalls aren’t blocking connections.
Guacamole Alternatives and Comparisons
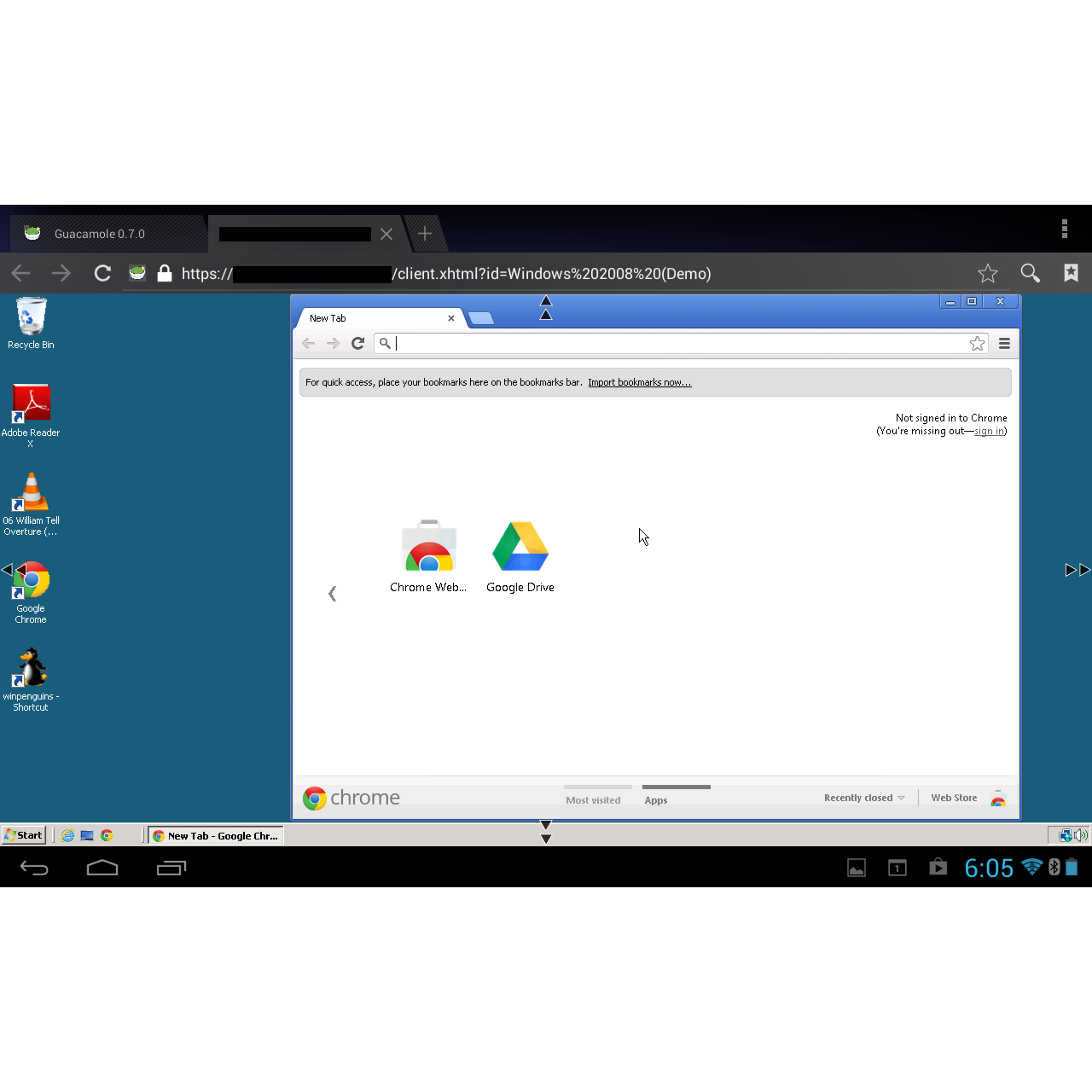
Guacamole is a fantastic open-source solution, but it’s not the only game in town when it comes to remote desktop gateways. Several other options exist, each with its own strengths and weaknesses. Choosing the right one depends heavily on your specific needs and infrastructure. This section will compare Guacamole to some popular alternatives, helping you make an informed decision.
A direct comparison requires considering factors like supported protocols, security features, ease of use, scalability, and integration capabilities. While Guacamole excels in certain areas, others might be better suited for specific use cases. The following table summarizes key differences.
Comparison of Open-Source Remote Desktop Gateway Solutions
| Feature | Guacamole | NoVNC | TightVNC | x2go |
|---|---|---|---|---|
| Supported Protocols | VNC, RDP, SSH, Telnet, and more | VNC | VNC | RDP, VNC, X11 |
| Security Features | SSL/TLS encryption, authentication integration | SSL/TLS encryption (often requires separate configuration) | SSL/TLS encryption (often requires separate configuration) | SSL/TLS encryption, user authentication |
| Ease of Use/Installation | Relatively easy to install and configure, good documentation | Can be more challenging to set up and configure, especially for complex environments | Simple client-side installation, server-side setup can be more complex. | Moderate complexity; requires more technical expertise than Guacamole. |
| Scalability and Performance | Highly scalable with proper configuration; performance depends on server resources and network conditions | Scalability depends on implementation; can be resource-intensive | Scalability depends on network and server configuration; performance varies widely. | Scalability is decent, but performance can be impacted by network latency. |
| Integration with Other Systems | Good integration possibilities through its API and extensibility | Limited integration capabilities | Limited integration capabilities; mainly used as a standalone solution. | Offers better integration options than NoVNC or TightVNC, but less than Guacamole. |
| Strengths | Broad protocol support, strong security, good scalability, extensive documentation and community support. | Lightweight, simple VNC implementation. | Widely used and well-established, simple client. | Good performance for X11 forwarding, supports multiple protocols. |
| Weaknesses | Can be resource-intensive depending on the number of concurrent connections. | Limited protocol support, security configuration can be complex. | Security heavily relies on proper configuration, limited features. | Steeper learning curve than Guacamole. |
Guacamole Use Cases and Best Practices
Apache Guacamole’s versatility makes it a valuable tool across various sectors. Its ability to provide secure remote access to a wide range of applications and systems makes it a compelling solution for organizations needing robust and flexible remote desktop capabilities. This section will explore practical applications and best practices for successful Guacamole deployments.
Real-World Guacamole Use Cases
Guacamole finds applications in diverse industries, addressing unique needs. For example, in healthcare, Guacamole enables secure remote access to patient records and medical imaging systems for authorized personnel, improving collaboration and reducing the risk of data breaches. In finance, it facilitates secure remote access to trading platforms and sensitive financial data, ensuring compliance and maintaining operational continuity. Manufacturing utilizes Guacamole for remote monitoring and control of industrial machinery and processes, enabling efficient troubleshooting and reducing downtime.
Educational institutions leverage Guacamole to provide students with remote access to lab equipment and specialized software, fostering learning opportunities regardless of location. Finally, help desks often use Guacamole to provide remote support to end-users, troubleshooting issues and resolving problems efficiently.
Best Practices for Guacamole Deployment and Management
Successful Guacamole implementation requires careful planning and execution. Prioritize robust security measures, including strong authentication mechanisms, encryption, and regular security audits. Establish clear access control policies, defining which users have access to which resources. Implement a comprehensive monitoring strategy to track performance, identify potential issues, and ensure system stability. Regularly update Guacamole and its underlying components to patch security vulnerabilities and benefit from performance improvements.
Finally, thorough documentation of the deployment, including configuration details and troubleshooting steps, is crucial for long-term maintainability and ease of support.
Optimizing Guacamole for Helpdesk Support
For helpdesk scenarios, optimizing Guacamole involves focusing on speed and ease of use. Employing a fast and reliable network infrastructure is paramount. Pre-configuring common connection profiles simplifies the support process. Integrating Guacamole with the helpdesk ticketing system streamlines workflow and enhances tracking. Providing clear and concise documentation for end-users facilitates independent troubleshooting and reduces support tickets.
Regular testing of the Guacamole setup ensures its responsiveness and reliability under pressure, maintaining a positive user experience. Consider using a dedicated Guacamole server optimized for the anticipated load to guarantee quick response times. A well-defined escalation path is also vital for handling complex issues that may require intervention from higher-level support personnel.
Final Thoughts
From its flexible architecture to its robust security features, Apache Guacamole offers a compelling solution for modern remote access needs. By understanding its core components and best practices, you can effectively implement and manage a secure and scalable remote desktop gateway. Whether you’re a seasoned sysadmin or a curious developer, Guacamole’s versatility and open-source nature make it a worthwhile tool to explore and master for streamlined remote access and management.
Query Resolution
What’s the difference between Guacamole and a traditional VPN?
VPNs create a secure tunnel for all your network traffic, while Guacamole focuses specifically on providing secure remote desktop access. Guacamole is generally simpler to set up and manage for this specific task.
Can Guacamole handle thousands of concurrent users?
Yes, but proper scaling and optimization are crucial. This often involves load balancing and careful resource allocation on the server-side.
Is Guacamole suitable for mobile devices?
Absolutely! Its web-based interface works seamlessly across various devices, including smartphones and tablets.
How does Guacamole handle authentication?
Guacamole supports various authentication methods, including local users, LDAP, and Kerberos, offering flexibility in integrating with existing security infrastructure.
What are some common troubleshooting steps if I can’t connect?
First, verify server connectivity and Guacamole service status. Then check your connection settings (protocol, hostname, credentials), and ensure the remote server is accessible and properly configured.
